This blog is a walk through to setup vSan encryption data-at-rest and VM/VMcrypt encryption with the vSphere native key provider.
Data-at-Rest encryption in a vSphere environment can occur either inside a virtual machine such as VM Encryption or can be by a storage system such as vSAN Data-at-Rest Encryption. If there is a need to encrypt just a few VMs, VM Encrypt may be a fit. Below diagram should help with pros and cons

Setup vSAN encryption with data-at-rest using the vSphere native key provider
Official VMware article
https://core.vmware.com/resource/vsan-encryption-services
Login to vCenter > click your vCenter at the top > Click configure tab > under security click key providers > Click add native key provider

Type in your native key provider name, ensure TPM is selected in tick box, Click add key provider (ensure TPM is supported on your hosts, most are)
(Use the below commands on each host if using an external KMS)
esxcli system settings encryption set –mode=TPM
esxcli system security keypersistence enable

Select your key provider and click back-up
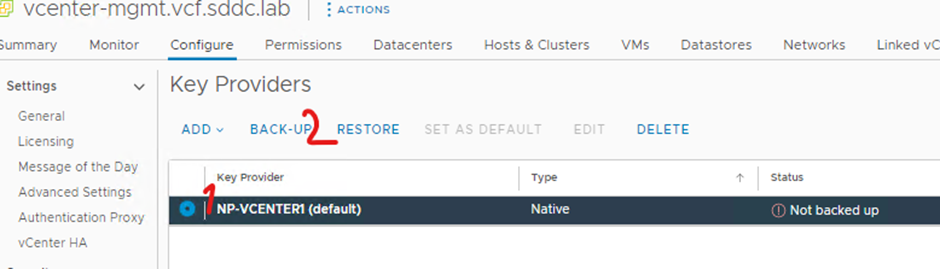
Click protect NKP with password and click back up key provider

Type in your password and click I saved the password in a secure pace and click back up key provider
(password will be needed if you ever restore vCenter)


Click your cluster, click configure, click services under vSan, click edit under Data Services
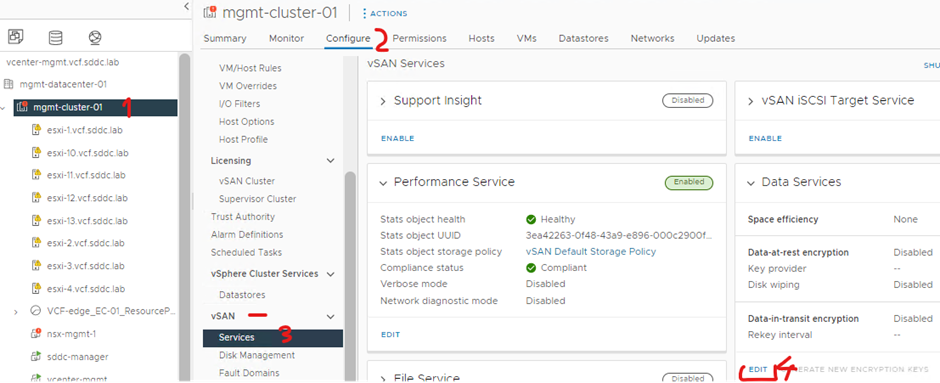
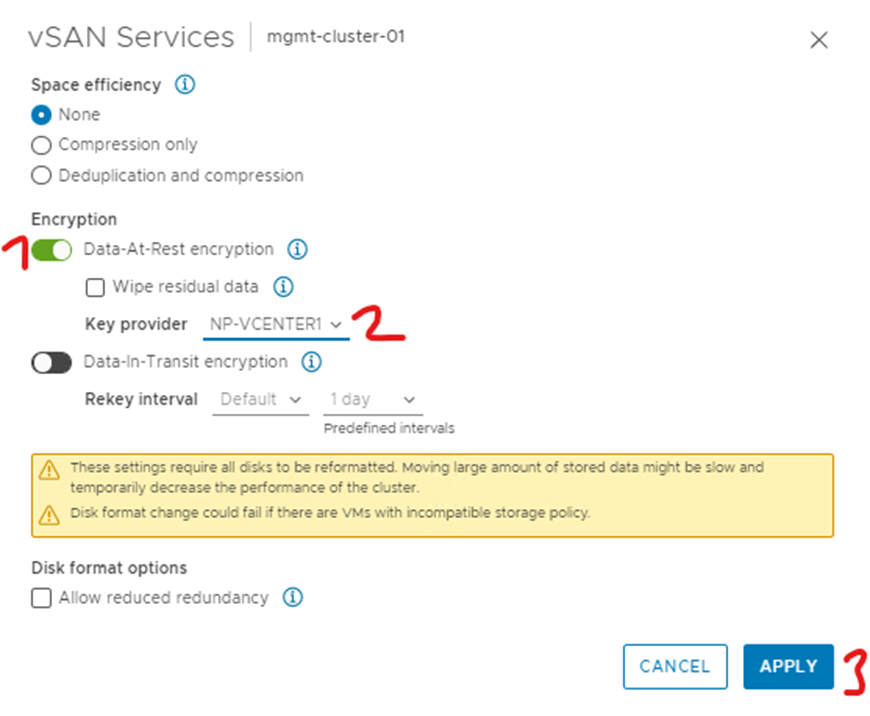
Turn on data-at-rest encryption and select your key provider and click apply
(Don’t select wipe residual data as this will remove existing data)
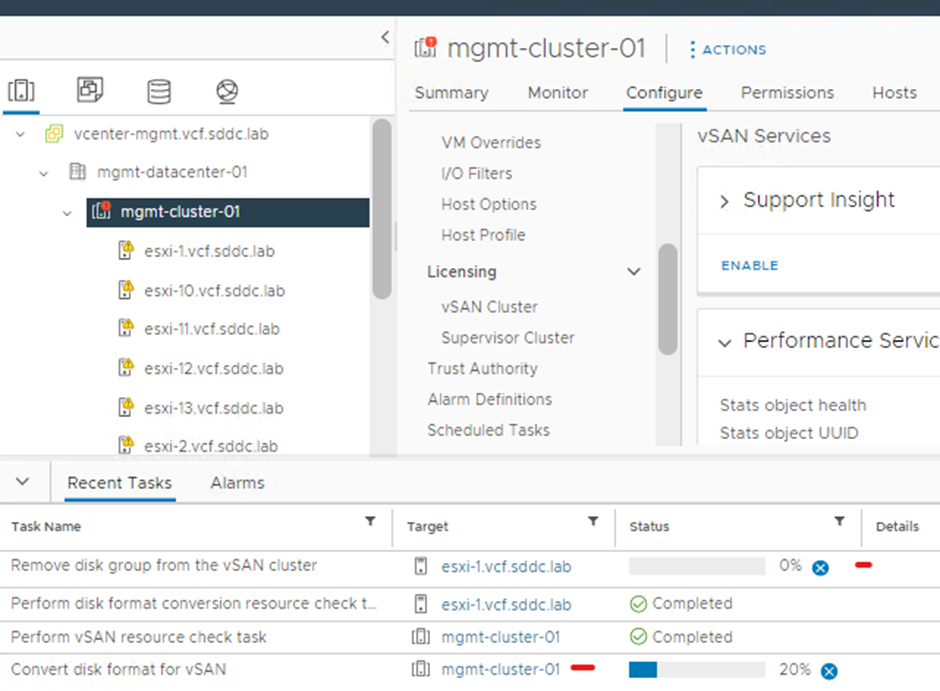
Disk groups will be recreated on each host one by one
Setup VM/VMcrypt encryption with NKP (for virtual machines)
Official VMware article
Login to vCenter > click your vCenter at the top > Click configure tab > under security click key provider > Click add native key provider

Type in your native key provider name, ensure TPM is selected in tick box, Click add key provider (ensure TPM is supported on your hosts, most are)
(Use the below commands on each host if using an external KMS)
esxcli system settings encryption set –mode=TPM
esxcli system security keypersistence enable

Select your key provider and click back-up

Click protect NKP with password and click back up key provider

Type in your password and click I saved the password in a secure pace and click back up key provider
(password will be needed if you ever restore vCenter)


vSphere has default encryption storage polices you can use, also VM needs to be turned off if you want to enable or disable encryption on it
Power off virtual machine > right click virtual machine > select VM Policies > click edit VM storage Polices

In the drop down on VM storage Policy select the encryption policy (VM Encryption Policy) and click ok
(The policy will be greyed out if no KMS/NKP is setup)

Edit settings of your virtual machine and you will see it is encrypted
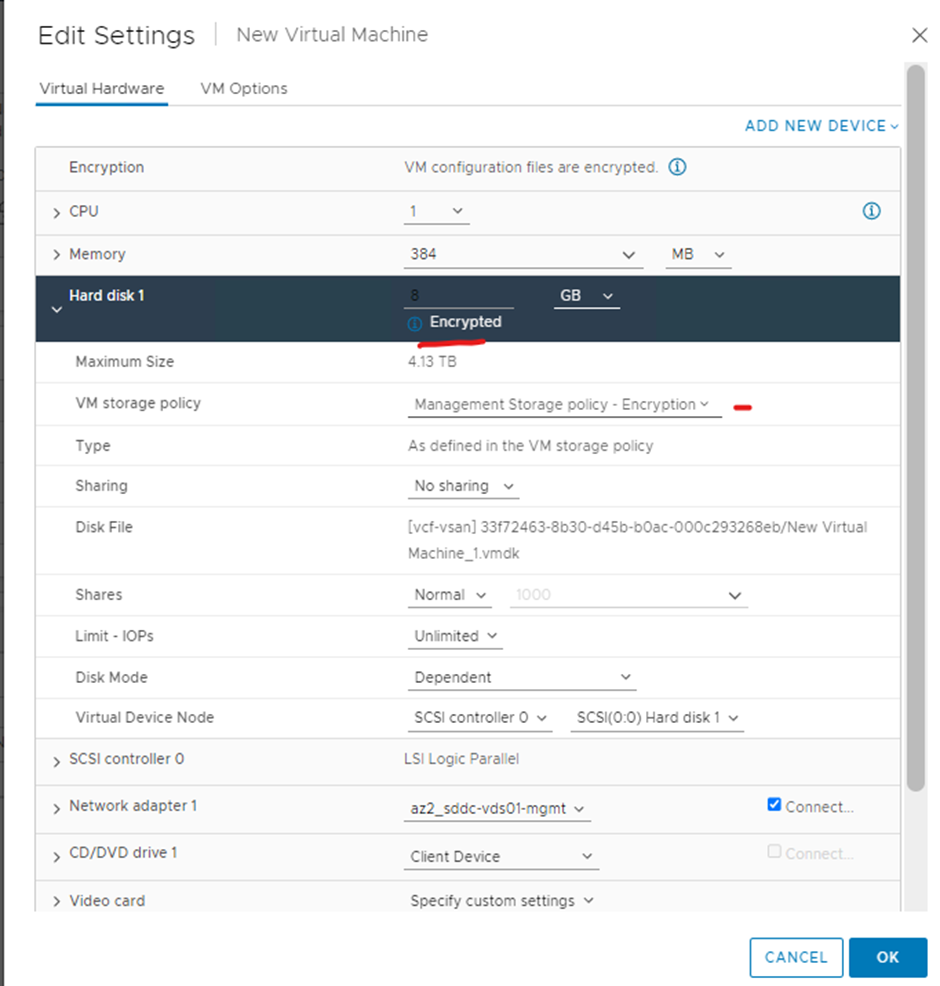
You can now power-on your virtual machine
If you want to create a new storage policy for VM encryption
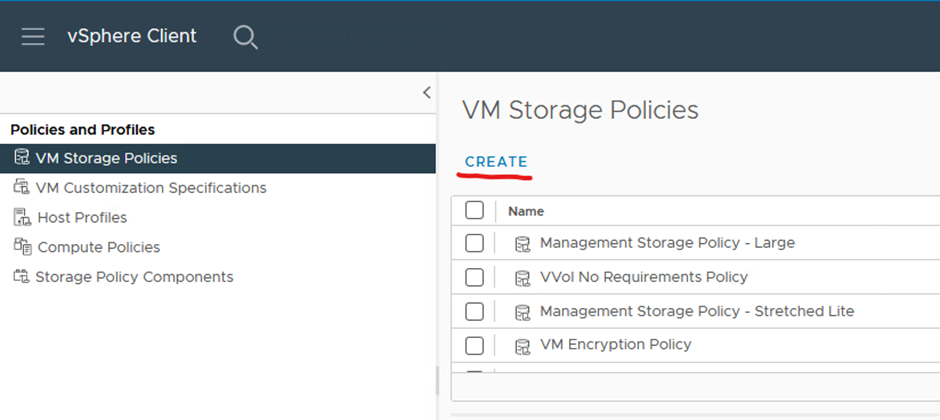
In vCenter click the three line and click Policies and Profiles

Click create
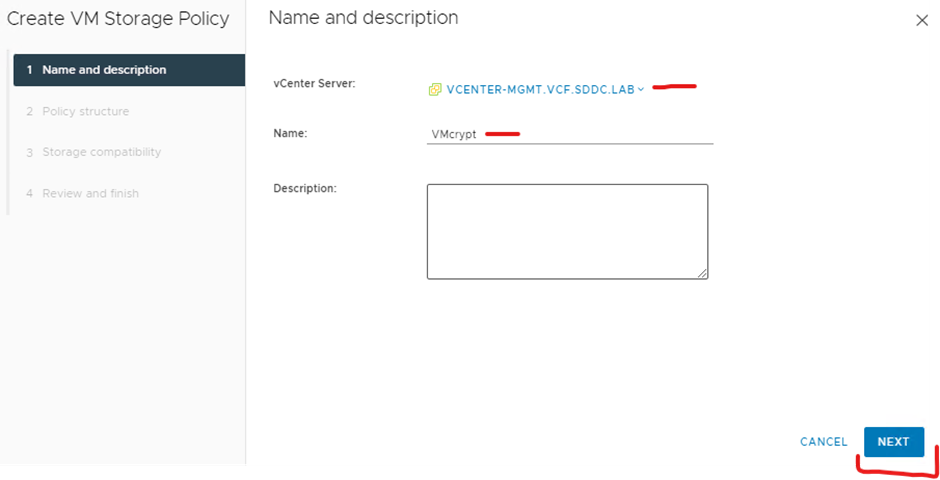
Select your vcenter and type a name for your policy and click next


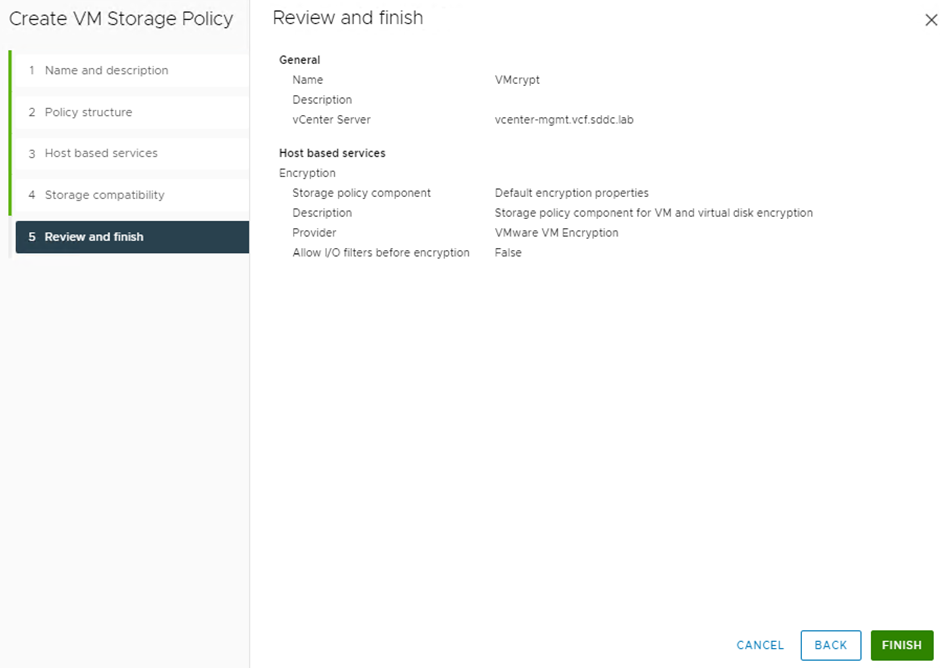
ensure your storage is compatible and click next

Click finish
Extra notes for vSAN data-at-rest encryption
Can be turned off disk groups get recreated again
vSAN encryption encrypts everything in the vSAN datastore. All files are encrypted, so all virtual machines and their corresponding data are protected
TPM option should be enabled if supported by the esxi host as this allow the key to on the esxi rather then getting it from the KMS
KMS should not be on the same vSAN that is being encrypted
Wipe option Should NOT be select as this will delete all existing data
Password should be saved somewhere safe for the NKP setup
Sftp backups also backup the native kms
During enablement of data-at-rest encryption each host disk group will be recreated it may take a while (One host at a time)
TPM should be supported and a minimum of version 2.0 on each host and should be checked before enabling data-at-rest.
Check all VM’s ensure they have a valid storage policy and check compliance as turning on data-at-rest might fail otherwise
Only admins can perform encryption and decryption tasks
Use the below commands on each host if using an external KMS
esxcli system settings encryption set –mode=TPM
esxcli system security keypersistence enable
This will allow Encryption operations to continue when the key server is unavailable, because the keys have persisted in the TPM. Key persistence is enabled by default when using the vSphere NKP, but when using an external KMS solution, will require enabling it through the following esxcli commands. The ESXi hosts can persist the encryption keys even after a reboot.
Same NKP can be imported to other vCenters such as other vCenters in linked mode (use the restore option in vCenter)
Best practice is to have separate NKP for each vCenter to control blast radius if issues occur.
Core dumps that are included in the vm-support package are also encrypted. GSS might ask you to decrypt the core dump
TPM Host private Keys will be stored in a security enclave(on hardware), which is encrypted with TPM stored keys
You will need your encryption key for restores of vCenter