The below process was tested on VCF 4.4.1.0 and in my lab I have only a root ca certificate and no intermediate certificates.
After a VCF bring up the ESXi hosts are singed with VMCA certificates, you can manually add external CA signed certificates to the hosts even after VCF has already been deployed and they will also be retained after an update through VCF.
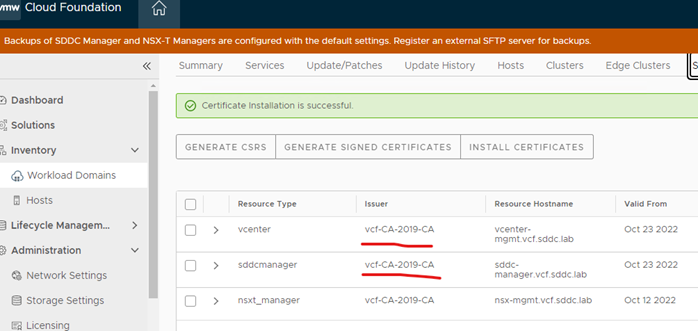
SDDC manager
If you have already signed your SDDC manager with an external CA certificate this is just a verification that the rootca and issuer is located there. This is the one you are going to use for the ESXi hosts.
Refer to the following link if you need to update your sddc manager certificates
- ssh to sddc manager
- su into sddc manager
- type in the below to get the keystore password
cat /etc/vmware/vcf/commonsvcs/trusted_certificates.key

- Type in the below with the keystore password
keytool -list -v -keystore /etc/vmware/vcf/commonsvcs/trusted_certificates.store
Ensure your root ca and issuer is in that list, in my case I have only the root CA use the serial number and the issuer name to confirm

Further checks in SDDC manager UI
Certificate on the browser
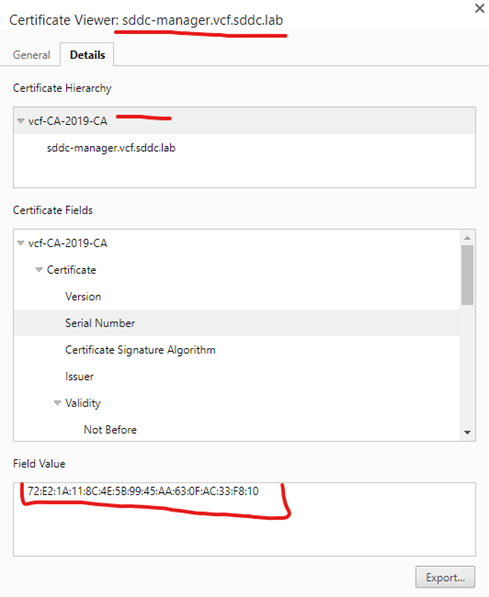
vCenter
This is just a verification that the root ca and intermediate certificates you are going to use on your ESXi hosts are on the vCenter server.
If your vCenter Server system is running the custom certificates issued by the same CA as those installed on the ESXi hosts you don’t have to import it into vCenter.
Refer to the following link if you need to update your vCenter manager certificates
/usr/lib/vmware-vmafd/bin/dir-cli trustedcert list
Type in SSO password

Also confirm your vCenter setting is setup for custom certificate in the advanced settings
Login to vCenter > click vCenter > click configure > click advanced settings > click edit > find vpxd.certmgmt.mode > modify to custom > click save
vpxd.certmgmt.mode = custom
old settings

New settings

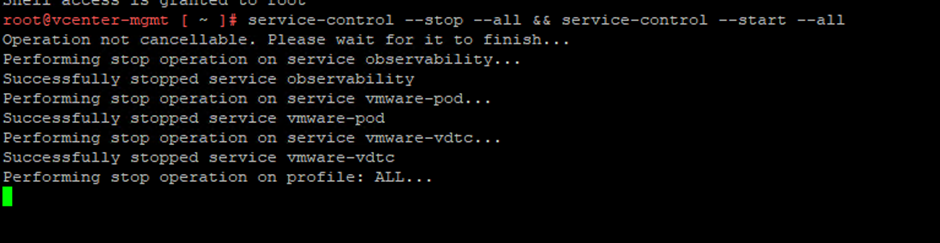
Then restart the services on vCenter
service-control –stop –all
service-control –start –all
ESXI host
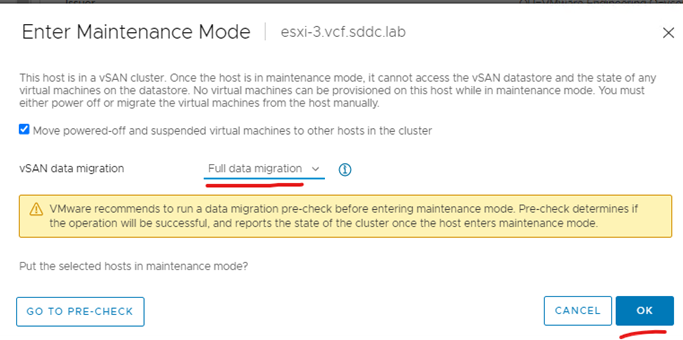
Enter maintenance mode on the host > full data migration
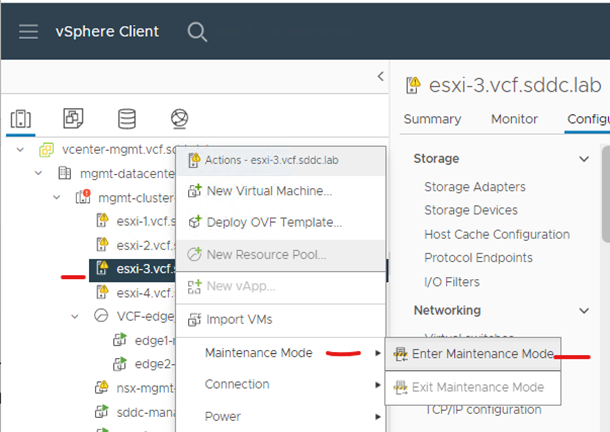
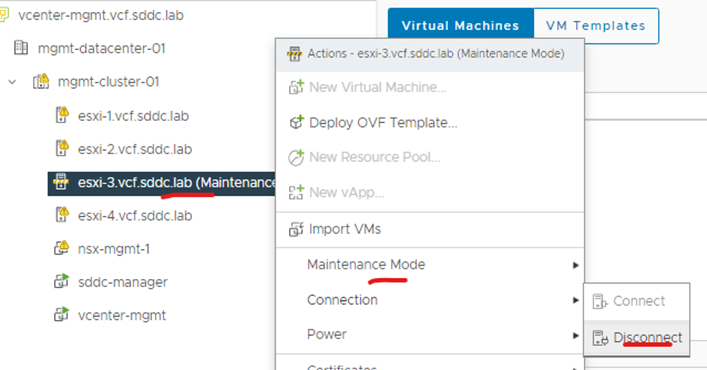
Disconnect ESXi host from vCenter
Create a .cfg file in bin directory of openssl use the below content to create the file
Name of file
esxi-3.vcf.sddc.lab.cfg
Content template – modify it to your organization setting
[ req ]
default_bits = 2048
default_keyfile = rui.key
distinguished_name = req_distinguished_name
encrypt_key = no
prompt = no
string_mask = nombstr
req_extensions = v3_req
[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = digitalSignature, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth, clientAuth
subjectAltName = DNS:esxi-3.vcf.sddc.lab
[ req_distinguished_name ]
countryName = AU
stateOrProvinceName = Victoria
localityName = Melbourne
0.organizationName = VMware
organizationalUnitName = VMware Local
commonName = esxi-3.vcf.sddc.lab

In the openssl bin folder type
openssl req -new -nodes -out rui.csr -keyout rui-orig.key -config esxi-3.vcf.sddc.lab.cfg

openssl rsa -in rui-orig.key -out rui.key

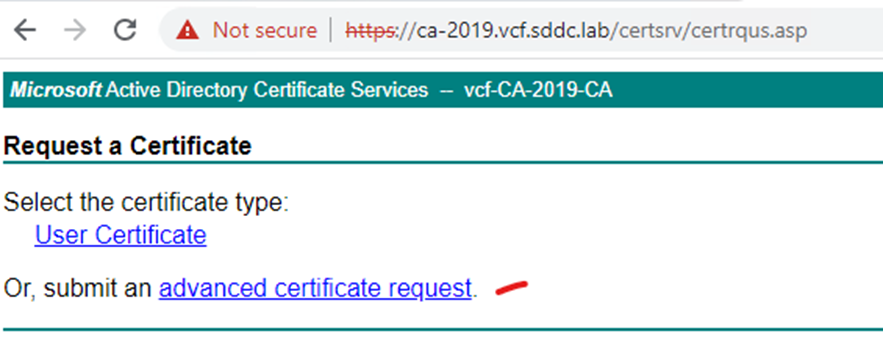
Get your business to sign the CSR and download full certificate chain – I am using Microsoft certificate authority in this example




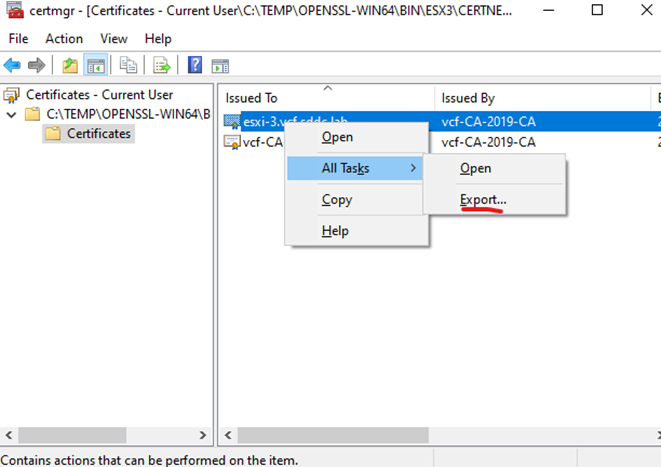
Export certificate chain – server certificate, root certificate and intermediate certificates (Always export as Base-64)

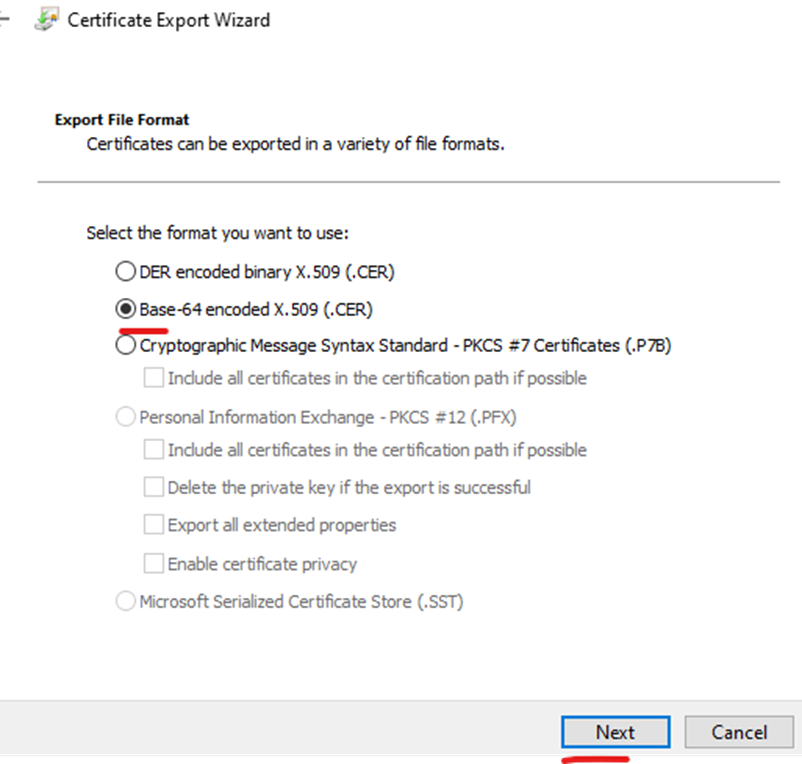






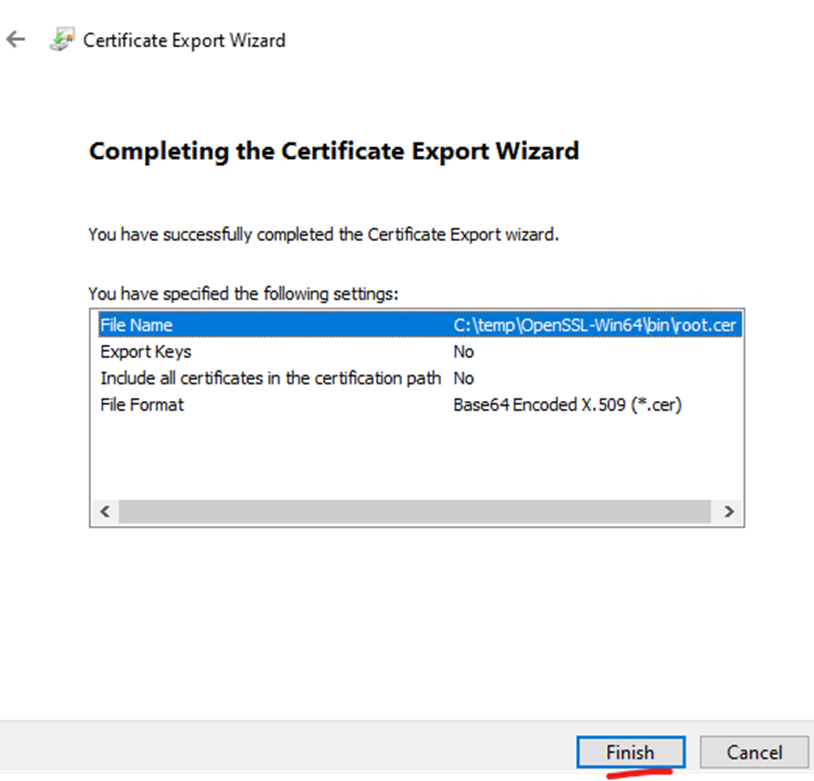
Edit rui.cer in notepad and rename to rui.crt
Include intermediate certificates in the root.cer if any, they should be on top of the root ca certificate

Put any intermediate certificates on top of your root ca

Run the following make sure they match
openssl rsa -modulus -noout -in rui.key
openssl x509 -modulus -noout -in rui.crt

Take a backup of existing certificates
ssh to ESXi host
cd /etc/vmware/ssl
mv rui.crt orig.rui.crt
mv rui.key orig.rui.key
cp /etc/vmware/ssl/castore.pem /etc/vmware/ssl/castore.pem.bak

copy out orig.rui.key,orig.rui.crt, castore.pem.bak to your machine use winscp, this is a backup if rollback is needed

copy root.cer via winscp to /etc/vmware/ssl/

Append the castore.pem file with your root.cer information
cat root.cer >> /etc/vmware/ssl/castore.pem
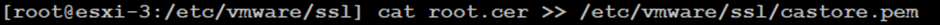
copy rui.crt and rui.key from winscp to /etc/vmware/ssl/
Run the below to save the information on your ESXi host
/sbin/auto-backup.sh

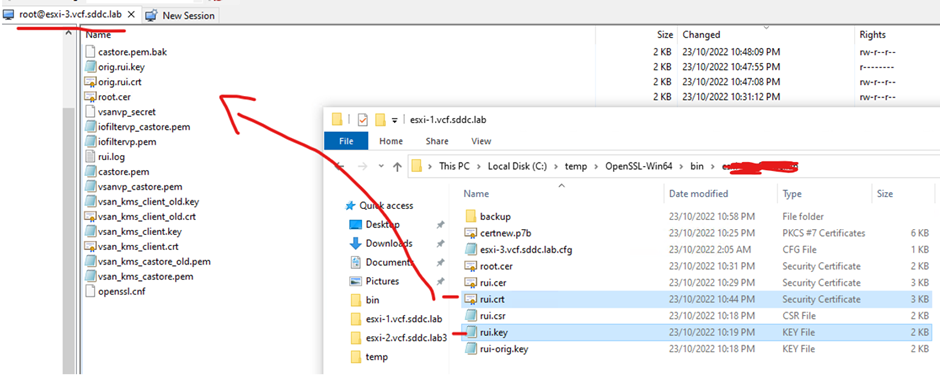
Restart agents
/etc/init.d/hostd restart && /etc/init.d/vpxa restart
Confirm ESXi UI is started if you want to login to the ESXi page
/etc/init.d/esxui status

Validate castore and rui.crt with each other
openssl verify -purpose sslclient -CAfile /etc/vmware/ssl/castore.pem /etc/vmware/ssl/rui.crt
openssl verify -purpose sslserver -CAfile /etc/vmware/ssl/castore.pem /etc/vmware/ssl/rui.crt

Type reboot
Once up check certificate from ESXi UI
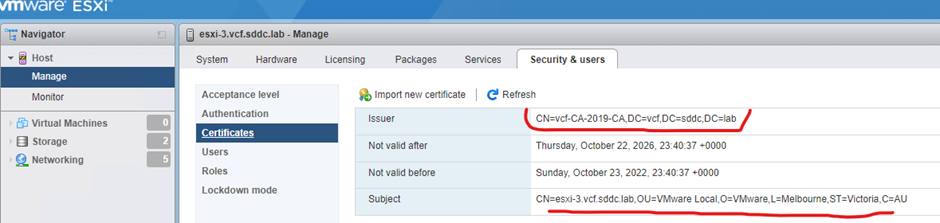
Connect ESXi host back through vCenter and take out of maintenance mode
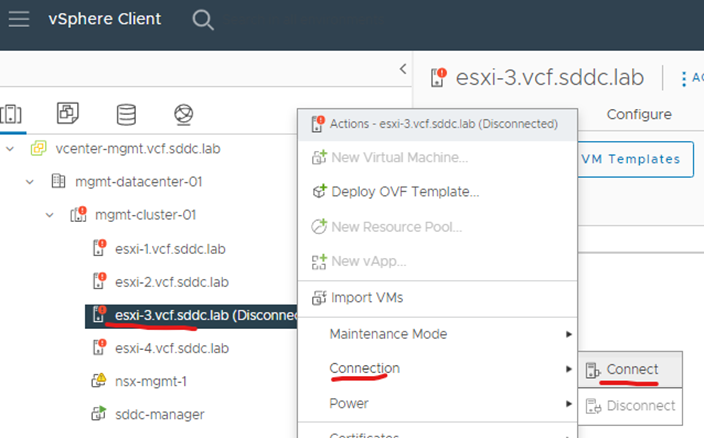

Confirm certificate through vCenter

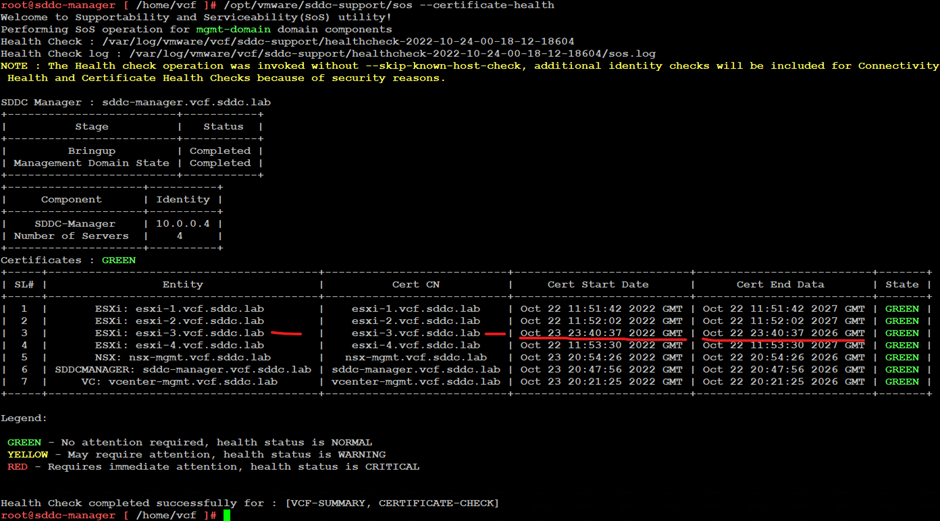
Check certificate health on SDDC manager
ssh to sddc manager
su
/opt/vmware/sddc-support/sos –certificate-health
More information
https://kb.vmware.com/s/article/56441
Please note if you don’t have your issuer and root ca installed on your computer and browser, the certificate in your browser wont show the full chain. You will not see the issuer or root ca certificate. You will also need to use the fqdn when browsing to the esxi host https://esxfqdn/ui.
Below example
